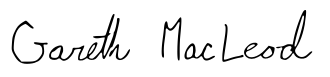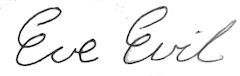Once you understand the fundamentals of Bitcoin, in particular the public transaction log thatanyone can submit transactions to called the Blockchain, there are some fairly obvious questions that follow. First among these is something like “If anyone can submit transactions to the blockchain, what’s to stop someone else from spending my bitcoins?”
Once you understand the fundamentals of Bitcoin, in particular the public transaction log thatanyone can submit transactions to called the Blockchain, there are some fairly obvious questions that follow. First among these is something like “If anyone can submit transactions to the blockchain, what’s to stop someone else from spending my bitcoins?”
It’s a good question with a really good answer.
One of the fundamentals of modern computer security is a system called “Public/Private Key Cryptography”. This system allows people to make signatures on digital goods that only they can make. You can sign documents, images, or bitcoin transactions on your computer in a way that is impossible for anyone else to replicate.
Public/Private Key cryptography works by giving everyone two numbers, called a “Public Key” and a “Private Key”. As the name implies, I tell everyone my public key, but I keep my private key secret. To make a signature, I “sign” a document using my private key. After I publish the document, anyone who wishes to check that the author is really me can verify that the document carries my signature by using my public key. [The actual method of signing and verifying are mathematical processes which are not really important to the concepts involved.]
You could say that my private key is a special pen that is the only pen in the world that can make my signature. Then the public key is a “signature-verifier” tool. The public key can’t make my signature, but it can be used to verify that a document carries my signature.
Bitcoins always have a public key attached to them in the blockchain. Only the person that can make the corresponding signature with their private key can submit transactions to the blockchain involving those bitcoins. When John sends bitcoins in a transaction to myself, the transaction, paraphrased from computer-speak, looks like this:
Transaction 25:
Here is John’s signature, therefore he can use the bitcoins sent to him in Transaction 24.
John is sending these bitcoins to Gareth, whose signature is this.
Then, when I send the same bitcoins to Ross, the transaction looks like this:
Transaction 26:
Here is Gareth’s signature, therefore he can use the bitcoins sent to him in Transaction 25.
Gareth is sending these bitcoins to Ross, whose signature is this:
When a computer in the bitcoin network hears about a new transaction through the network, it does a couple things. First, it looks up the historical transaction referenced in the new transaction (this is the part of the transaction that says “these bitcoins were sent to him in Transaction 25"). Then it compares the signature on the new transaction to the signatures on the old transaction in the blockchain. If the signatures match, the computer “confirms” the transaction by repeating it back to the network.
A hacker named Eve could try to broadcast a transaction involving my bitcoins, such as
Transaction 27:
Here is Gareth’s signature, therefore he can use the bitcoins sent to him in Transaction 25.
Gareth is sending these bitcoins to Eve, whose signature is this.
But anyone can see that the signature in Transaction 27 is not the same as my signature in Transaction 25, so it probably isn’t me sending this transaction. It’s equally easy for computers to see that the digital signature on a forged transaction does not match the signature stored in the blockchain, so any computer asked to confirm this transaction will reject it. The forged transaction will not be recorded in the blockchain and will be forgotten.
This is how the blockchain can be public but still secure. So long as only you have your private key, only you can make your signature, and no one will be able to make transactions involving your bitcoins that the rest of the computers in the network will accept. Only you can spend your bitcoins.
Practically speaking, you will never have to worry about this because your signatures are managed by your wallet program and you never have to see nor think about them.
Hopefully this has given you more confidence in the security of Bitcoin as a whole. Now you know that when you own bitcoins, no one can spend them except you.
If you have any more questions, or would like other topics about Bitcoin covered, feel free to tweet at me at @garethmacleod, or send me an email at [email protected].